 |
|
Please Whitelist This Site?
I know everyone hates ads. But please understand that I am providing premium content for free that takes hundreds of hours of time to research and write. I don't want to go to a pay-only model like some sites, but when more and more people block ads, I end up working for free. And I have a family to support, just like you. :)
If you like The TCP/IP Guide, please consider the download version. It's priced very economically and you can read all of it in a convenient format without ads.
If you want to use this site for free, I'd be grateful if you could add the site to the whitelist for Adblock. To do so, just open the Adblock menu and select "Disable on tcpipguide.com". Or go to the Tools menu and select "Adblock Plus Preferences...". Then click "Add Filter..." at the bottom, and add this string: "@@||tcpipguide.com^$document". Then just click OK.
Thanks for your understanding!
Sincerely, Charles Kozierok
Author and Publisher, The TCP/IP Guide
|
|
|

Custom Search
|
|
IPSec General Operation, Components and Protocols
(Page 2 of 3)
IPSec Core Protocols
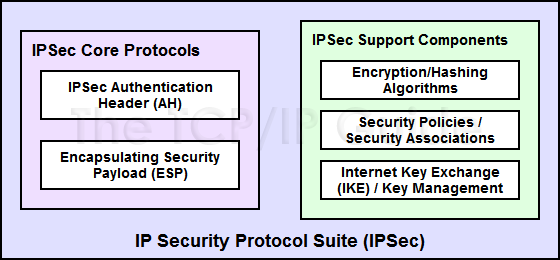
To support the activities above, a number of different components comprise the total package known as “IPSec”, as shown in Figure 116. The two main pieces are a pair of technologies sometimes called the core protocols of IPSec. These are the ones that actually do the work of encoding information to ensure security. They are:
- IPSec Authentication Header (AH): This
protocol provides authentication services for IPSec. What this means
is that it allows the recipient of a message to verify that the supposed
originator of a message was in fact the one that sent it. It also allows
the recipient to verify that none of the data in the datagram has been
changed by any intermediate devices en route. It also provides protection
against so-called “replay” attacks, where a message is captured
by an unauthorized user and re-sent.
- Encapsulating Security Payload (ESP):
The Authentication Header ensures integrity of the data in datagram,
but not its privacy. When the information in a datagram is “for
your eyes only”, it can be further protected using the ESP protocol,
which encrypts the payload of the IP datagram.
Figure 116: Overview of IPSec Protocols and Components
|
| |||||||||||||||||||
Home - Table Of Contents - Contact Us
The TCP/IP Guide (http://www.TCPIPGuide.com)
Version 3.0 - Version Date: September 20, 2005
© Copyright 2001-2005 Charles M. Kozierok. All Rights Reserved.
Not responsible for any loss resulting from the use of this site.






